HowTo Use The Scapy: Multi-Traceroute - MTR
Overview

SVN: 7683
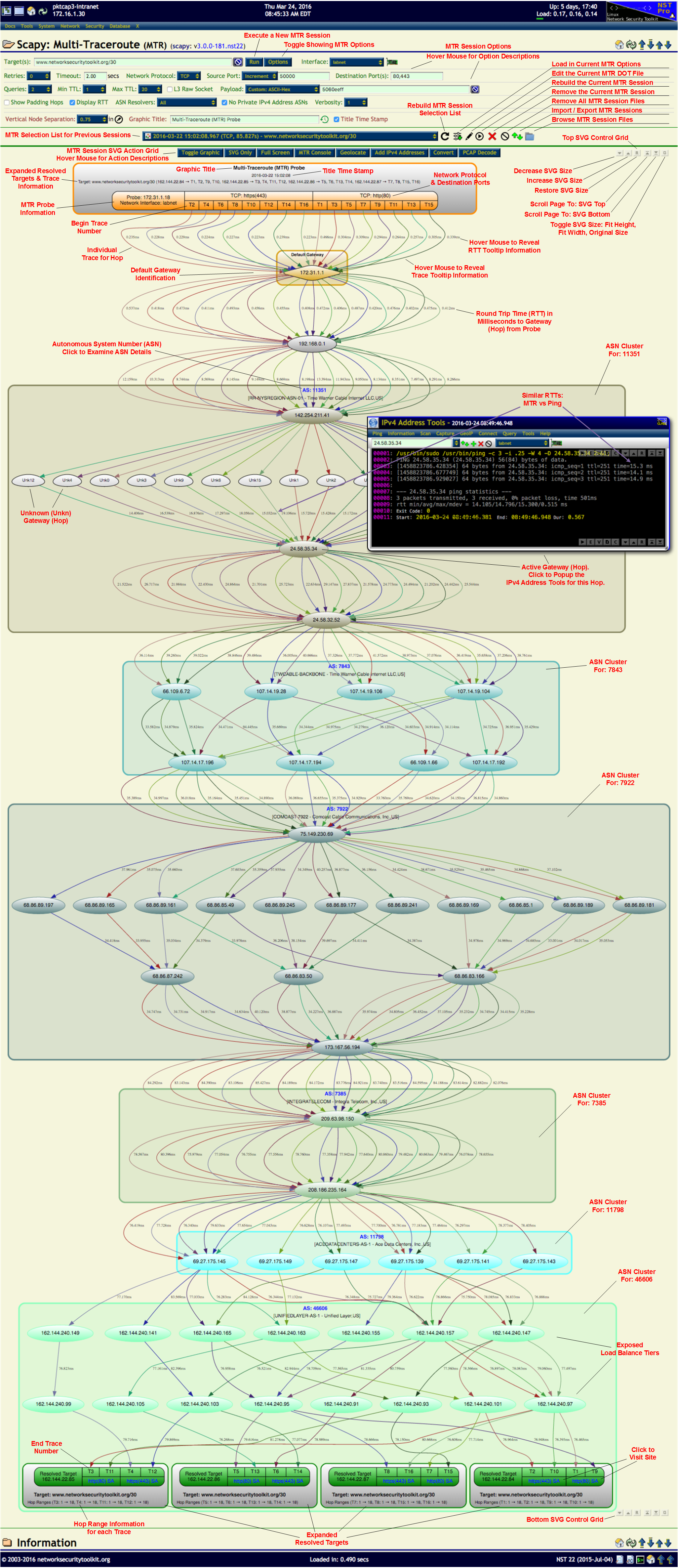
A new Multi-Traceroute (MTR) networking tool has been developed for NST 22. This tool provides an interactive Traceroute visual using Scapy similar to the Traceroute Command and has been integrated into the NST WUI. NST uses the Python 3 version of Scapy known as Scapy3k.
A new Scapy3k command: mtr (Multi-Traceroute) has been developed. It is an enhanced version of the original Scapy traceroute command. It includes new features such as running multiple queries with each target, display of Round Trip Time (RTT) calculations, selection of using Network Protocols: TCP, UDP and ICMP and enhanced SVG graphical results.
NST WUI enhancements include a GUI options interface, an interactive MTR SVG graphic, NST IPv4 Address Tool integration.
Simple Trace
Using the Scapy Multi-Traceroute page can be as simple as entering the host name you want to perform the trace on (www.techhounds.com in the example below) and pressing the Run button.
Once the trace completes you will get a graphical chart (as an SVG image shown below) that contains:
- The list of IP addresses exposed by the trace (clicking on an IP address will bring up the IP tools widget).
- Time measurements from the source to each segment of the trace.
- ASN groupings (when possible) of each segment of the trace.
<img src="http://wiki.networksecuritytoolkit.org/nstwiki/images/Scapy-mtr-simple.svg" style="width: 800px" alt="A simple Scapy Multi-Traceroute Example" />
Complex Trace
<img src="http://wiki.networksecuritytoolkit.org/nstwiki/images/Mtr_overview.svg" style="width: 600px" alt="MTR Overview SVG Graphic" />
Scapy: Multi-Traceroute (MTR) Reference Document