NST Heartbleed Detection
Overview
![]() This page shows how to use NST and nmap to detect the heartbleed vulnerability. Heartbleed is a software bug in the open-source cryptography library OpenSSL, which allows an attacker to read the memory of the host computer, allowing them to retrieve potentially privacy-sensitive data.
This page shows how to use NST and nmap to detect the heartbleed vulnerability. Heartbleed is a software bug in the open-source cryptography library OpenSSL, which allows an attacker to read the memory of the host computer, allowing them to retrieve potentially privacy-sensitive data.
See the following sites for technical details on this vulnerability:
- CVE (Common Vulnerabilities and Exposures) CVE-2014-0160
- OpenSSL Security Advisory 20140407
- CVE Details
- http://heartbleed.com/
- xkcd Heartbleed Explanation
Heartbleed Detection - NST Pro System

SVN: 5804
NST Pro users need to first update their NST system to get the latest version of nmap (i.e., v6.45 or greater) from the NST Pro repository. This release contains the nmap NSE (Nmap Scripting Engine) script: "/usr/share/nmap/scripts/ssl-heartbleed.nse" written by Patrik Karlsson which is based on code authored by Jared Stafford.
Yum update you NST Pro system.
. . . ==================================================================================================================================== Package Arch Version Repository Size ==================================================================================================================================== Updating: nmap i686 2:6.46-32841.10.nst20 NstPro 3.9 M Updating for dependencies: nmap-frontend noarch 2:6.46-32841.10.nst20 NstPro 685 k nmap-ncat i686 2:6.46-32841.10.nst20 NstPro 124 k Transaction Summary ==================================================================================================================================== . . .
Command Line
The following is an example nmap command for the detection of the "Heartbleed" vulnerability on host: "10.21.23.19" port: "443 (https)"
Starting Nmap 6.45 ( http://nmap.org ) at 2014-04-11 19:07 EDT Nmap scan report for 10.21.23.19 Host is up (0.00024s latency). PORT STATE SERVICE 443/tcp open https | ssl-heartbleed: | VULNERABLE: | The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. It allows for stealing information intended to be protected by SSL/TLS encryption. | State: VULNERABLE | Risk factor: High | Description: | OpenSSL versions 1.0.1 and 1.0.2-beta releases (including 1.0.1f and 1.0.2-beta1) of OpenSSL are affected by the Heartbleed bug. The bug allows for reading memory of systems protected by the vulnerable OpenSSL versions and could allow for disclosure of otherwise encrypted confidential information as well as the encryption keys themselves. | | References: | http://cvedetails.com/cve/2014-0160/ | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160 |_ http://www.openssl.org/news/secadv_20140407.txt MAC Address: 08:00:27:70:D5:9B (Cadmus Computer Systems) Nmap done: 1 IP address (1 host up) scanned in 0.54 seconds
NST WUI
This section shows the NST WUI Nmap page with scan options and results using the Nmap NSE script: "/usr/share/nmap/scripts/ssl-heartbleed.nse":
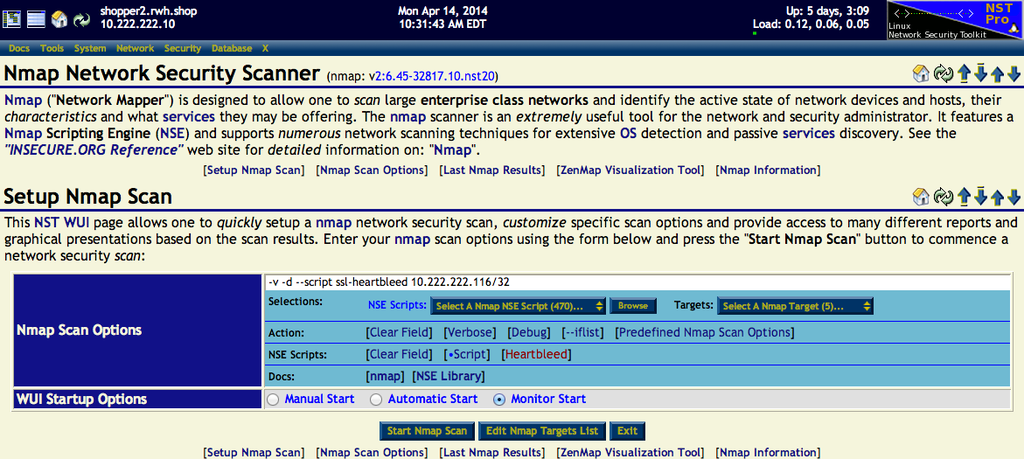
This host: "10.222.222.116" is vulnerable to heartbleed. The image below shows the Nmap scan results formatted with the Nmap XSL style sheet:
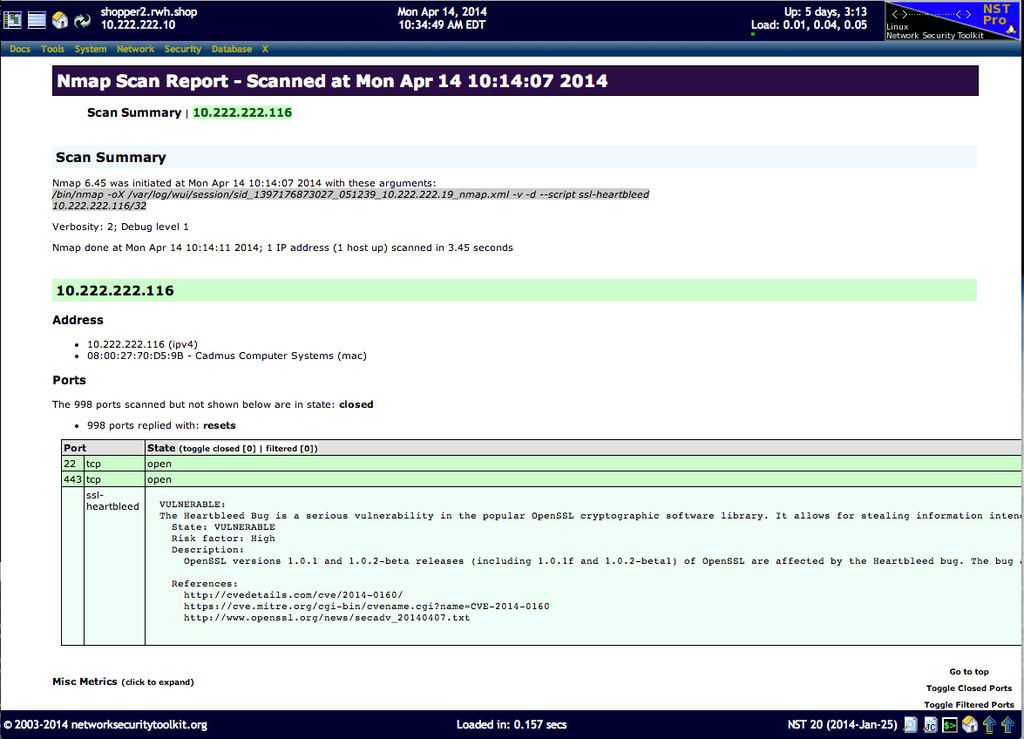
Heartbleed Detection - NST Public System
NST Public users will first need to manually update their NST 20 system from the nmap site: "https://svn.nmap.org" to allow for nmap heartbleed detection. The following command sequence shows the necessary steps to allow the nmap version shipped with NST 20 to run the heartbleed nmap NSE script: "/usr/share/nmap/scripts/ssl-heartbleed.nse". Backups are created for all nmap files updated just in case there are any errors.
Command Line
The following is an example nmap command for the detection of the "Heartbleed" vulnerability on host: "172.31.1.57" for all ports. Both debug and verbose output options were selected.
Starting Nmap 6.40 ( http://nmap.org ) at 2014-04-11 19:44 EDT
PORTS: Using top 1000 ports found open (TCP:1000, UDP:0, SCTP:0)
--------------- Timing report ---------------
hostgroups: min 1, max 100000
rtt-timeouts: init 1000, min 100, max 10000
max-scan-delay: TCP 1000, UDP 1000, SCTP 1000
parallelism: min 0, max 0
max-retries: 10, host-timeout: 0
min-rate: 0, max-rate: 0
---------------------------------------------
NSE: Using Lua 5.2.
NSE: Script Arguments seen from CLI:
NSE: Loaded 1 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 1) scan.
Initiating ARP Ping Scan at 19:44
Scanning 172.31.1.57 [1 port]
Packet capture filter (device labnet): arp and arp[18:4] = 0x000D6172 and arp[22:2] = 0x8175
Completed ARP Ping Scan at 19:44, 0.21s elapsed (1 total hosts)
Overall sending rates: 4.72 packets / s, 198.28 bytes / s.
mass_rdns: Using DNS server 172.31.1.19
mass_rdns: Using DNS server 172.31.1.1
Initiating Parallel DNS resolution of 1 host. at 19:44
mass_rdns: 0.00s 0/1 [#: 2, OK: 0, NX: 0, DR: 0, SF: 0, TR: 1]
Completed Parallel DNS resolution of 1 host. at 19:44, 0.00s elapsed
DNS resolution of 1 IPs took 0.00s. Mode: Async [#: 2, OK: 1, NX: 0, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 19:44
Scanning localhost.lab.univstech.com (172.31.1.57) [1000 ports]
Packet capture filter (device labnet): dst host 172.31.1.17 and (icmp or icmp6 or ((tcp or udp or sctp) and (src host 172.31.1.57)))
Discovered open port 22/tcp on 172.31.1.57
Discovered open port 443/tcp on 172.31.1.57
Increased max_successful_tryno for 172.31.1.57 to 1 (packet drop)
Completed SYN Stealth Scan at 19:44, 1.38s elapsed (1000 total ports)
Overall sending rates: 816.01 packets / s, 35904.48 bytes / s.
NSE: Script scanning 172.31.1.57.
NSE: Starting runlevel 1 (of 1) scan.
NSE: Starting ssl-heartbleed against 172.31.1.57:443.
Initiating NSE at 19:44
NSE: we're done!
NSE: Finished ssl-heartbleed against 172.31.1.57:443.
Completed NSE at 19:44, 0.02s elapsed
Nmap scan report for localhost.lab.univstech.com (172.31.1.57)
Host is up, received arp-response (0.0032s latency).
Scanned at 2014-04-11 19:44:31 EDT for 2s
Not shown: 998 closed ports
Reason: 998 resets
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
443/tcp open https syn-ack
| ssl-heartbleed:
| VULNERABLE:
| The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. It allows
for stealing information intended to be protected by SSL/TLS encryption.
| State: VULNERABLE
| Risk factor: High
| Description:
| OpenSSL versions 1.0.1 and 1.0.2-beta releases (including 1.0.1f and 1.0.2-beta1) of OpenSSL are affected
by the Heartbleed bug. The bug allows for reading memory of systems protected by the vulnerable OpenSSL versions
and could allow for disclosure of otherwise encrypted confidential information as well as the encryption keys
themselves.
|
| References:
| http://cvedetails.com/cve/2014-0160/
| http://www.openssl.org/news/secadv_20140407.txt
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
MAC Address: 00:0C:29:AD:9C:1B (VMware)
Final times for host: srtt: 3219 rttvar: 881 to: 100000
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 1) scan.
Read from /usr/bin/../share/nmap: nmap-mac-prefixes nmap-payloads nmap-services.
Nmap done: 1 IP address (1 host up) scanned in 1.79 seconds
Raw packets sent: 1130 (49.704KB) | Rcvd: 1130 (45.196KB)
Remediation Steps For An NST System
If one has access and admin privileges to the remote server that exhibits the heartbleed vulnerability, then one needs to update the OpenSSL libraries on that system.
For an NST system, one needs to Yum update the openssl RPM packages. The Fedora openssl RPM version: "1.0.1e-37.fc20.1" or greater contains a patch for "CVE-2014-0160". Follow the update with a system reboot or restart of Web services.
. . . ============================================================================================================================================= Package Arch Version Repository Size ============================================================================================================================================= Updating: openssl x86_64 1:1.0.1e-37.fc20.1 updates 705 k Updating for dependencies: openssl-devel x86_64 1:1.0.1e-37.fc20.1 updates 1.2 M openssl-libs x86_64 1:1.0.1e-37.fc20.1 updates 916 k Transaction Summary ============================================================================================================================================= Update 3 Packages . . .