Multi-Tap Network Packet Capturing: Difference between revisions
| Line 36: | Line 36: | ||
[[Image:Multi-tap_nic_enhanced.png|center|frame|NIC Adapter Information And Control]] | [[Image:Multi-tap_nic_enhanced.png|center|frame|NIC Adapter Information And Control]] | ||
Both interfaces are initially shown in the "'''Down'''" state indicated by the <span style="color: red;">red</span> down arrow. | Both interfaces are initially shown in the "'''Down'''" state indicated by the '''<span style="color: red;">red</span>''' down arrow superimposed on the "'''NIC Adapter'''" icons. The network interface will automatically be put in the "'''Up'''" state prior to starting a capture session. | ||
Revision as of 21:45, 2 July 2008
Overview
This section will demonstrate the use of Multi-Tap Network Packet Capture with NST. The NST WUI implementation supports simultaneous Packet Capture on up to 4 network interfaces (Quad Tap) per multi-tap capture session. NST uses the Wireshark network protocol analyzer suite for network packet capture. The light-weight network packet capture tool: "dumpcap" is used as the capture engine.
When capturing packets at Gigabit Ethernet rates and one needs total visibility on the link, then a passive tap is required. Net Optics, a global leader in passive monitoring, makes an excellent 10/100/1000BaseT Tap (TP-CU3) for passively allowing access to monitor GigaBit traffic.
Multi-Tap Network Packet Capture: NAT/PAT Traffic
The diagram depicted below shows an example Multi-Tap Capture Setup for monitoring GigaBit traffic across a firewall boundary. We will explore the capturing of packets as they transverse the firewall and undergo both Network and Port Address Translation.
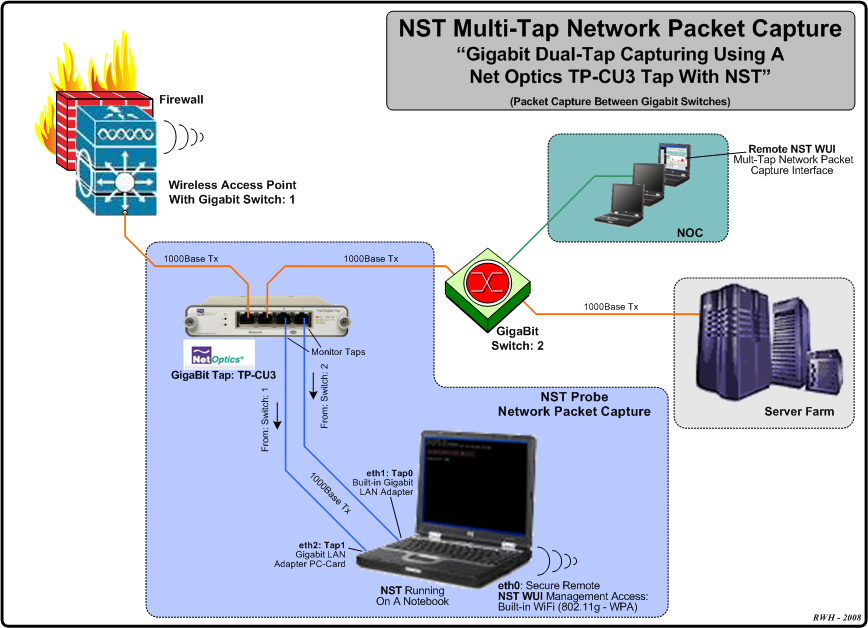
Multi-Tap Network Packet Capture: Traffic Between Gigabit Switches
The diagram displayed below shows an example Dual-Tap Capture Setup for monitoring network traffic between 2 Gigabit switches. In this case a generic notebook computer was used and configured with 3 network interfaces (A built-in Gigabit LAN adapter, a Gigabit LAN adapter PC-Card and a built-in 802.11g/n wireless adapter for secure remote access and control of NST).
Example Multi-Tap Network Packet Capture Session: Step-By-Step
This section will demonstrate a Multi-Tap Network Packet session using 2 network interfaces (eth1 and eth2) as the target capture interfaces. We will concentrate on email traffic (POP and SMTP). It is assumed that the NST probe has sufficient network interface adapters (at least 2 in this case) to perform this capture.
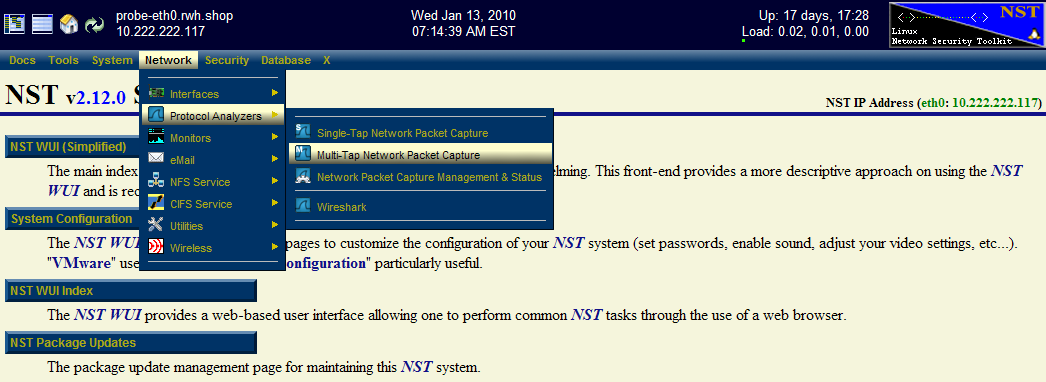
Step: 1 NST WUI Multi-Tap Network Packet Capture Page
From the NST WUI Start page go to the NST WUI Multi-Tap Network Packet Capture page. This is accomplished by using the NST WUI Menu. Go to "Networking" then "Protocol Analyzers" and then go to the "Multi-Tap Network Packet Capture" page as shown below.
Step: 2 Multi-Tap Interfaces & Data Directory Selection
Use the navigational aid link: "Select Tap Interfaces/Directory" to go to the "Multi-Tap Interfaces & Data Directory Selection" section. This is where you select the target capture interfaces and data directory on the NST probe when you will store your multi-tap capture.
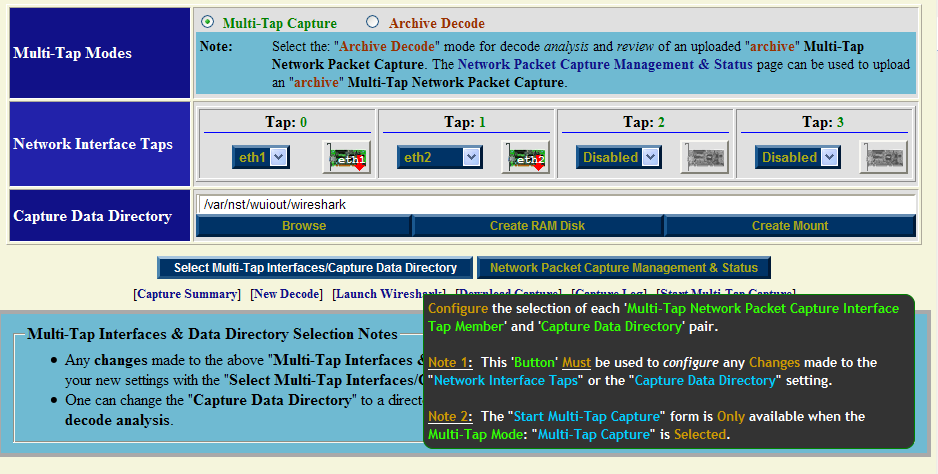
Select interface: "eth1" for Tap0 and select interface: "eth2" for Tap1. For now use the default capture data directory: "/var/nst/wuiout/wireshark". Your configuration should look similar to the NST WUI image caption above. Next select the "Select Multi-Tap Interfaces/Capture Data Directory" button to make your configuration known to NST.
One can click on a "NIC Adapter" icon to view and control a specific network interface adapter. The caption below shows information for NIC Adapter: "eth2" and results for running the "ifconfig eth2" and the "ethtool -i eth2" commands.
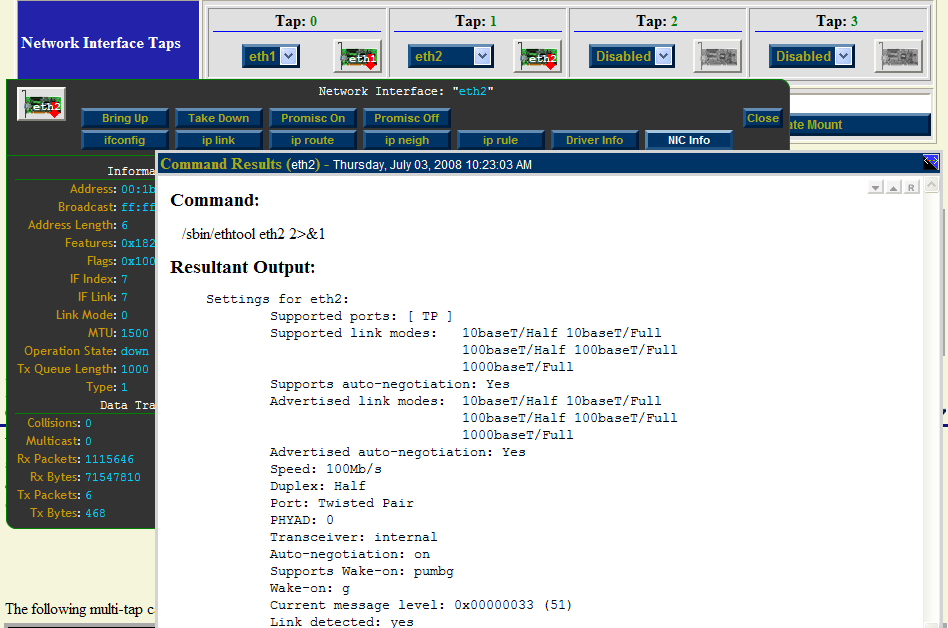
Both interfaces are initially shown in the "Down" state indicated by the red down arrow superimposed on the "NIC Adapter" icons. The network interface will automatically be put in the "Up" state prior to starting a capture session.