Multi-Tap Network Packet Capturing: Difference between revisions
No edit summary |
No edit summary |
||
| Line 4: | Line 4: | ||
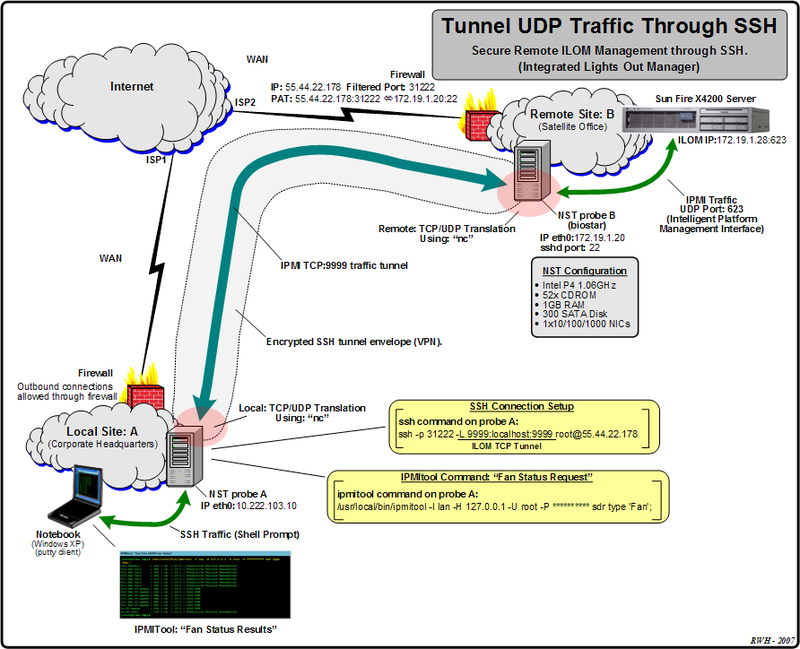
The diagram depicted below shows and example '''Multi-Tap Capture Setup''' for monitoring GigaBit traffic across a firewall boundary. We will explore the capturing of packets as they transverse the firewall and under go both '''Network''' and '''Port Address Translation'''. | The diagram depicted below shows and example '''Multi-Tap Capture Setup''' for monitoring GigaBit traffic across a firewall boundary. We will explore the capturing of packets as they transverse the firewall and under go both '''Network''' and '''Port Address Translation'''. | ||
[[Image:Nst udp ssh.png|center|thumb|800px|Network Topology]] | |||
Revision as of 10:28, 12 June 2008
This section with demonstrate the use of Multi-Tap Network Packet Capture with NST. The NST WUI implementation supports simultaneous Packet Capture on up to 4 network interfaces (Quad Tap) per multi-tap capture session. NST uses the Wireshark network protocol analyzer suite for network packet capture. The light-weight network packet capture tool: "dumpcap" is used as the capture engine.
When capturing packets at Gigabit Ethernet rates and one needs total visibility on the link, then a passive tap is required. Net Optics, a global leader in passive monitoring, makes an excellent 10/100/1000BaseT Tap (TP-CU3) for passively allowing access to monitor GigaBit traffic.
The diagram depicted below shows and example Multi-Tap Capture Setup for monitoring GigaBit traffic across a firewall boundary. We will explore the capturing of packets as they transverse the firewall and under go both Network and Port Address Translation.