Firewall Setup Tips: Difference between revisions
No edit summary |
|||
| (13 intermediate revisions by 2 users not shown) | |||
| Line 142: | Line 142: | ||
<div class="screen"> | <div class="screen"> | ||
<div class="screenTitle">Using quicktables-2.3</div> | <div class="screenTitle">Using quicktables-2.3</div> | ||
<div class="userInput"><span class="prompt">[root@tmobile ~]# </span>quicktables-2.3</div> | <div class="userInput"><span class="prompt">[root@tmobile ~]# </span>/usr/share/quicktables/quicktables-2.3</div> | ||
<pre class="computerOutput"> | <pre class="computerOutput"> | ||
| Line 313: | Line 313: | ||
</div> | </div> | ||
== Turning an NST Probe Into A Broadband Router == | |||
== Turning | |||
In many homes and small businesses, you will find a small broadband router (such as a ''LinkSys WRT54G''). The broadband router is typically configured to act as a firewall and perform Network Address Translation ('''NAT'''). This provides a layer of protection of the internal Local Area Network ('''LAN''') from the outside world. It allows systems on the '''LAN''' to initiate connections to the outside world, but blocks the outside world from initiating connections to systems within the '''LAN'''. | In many homes and small businesses, you will find a small broadband router (such as a ''LinkSys WRT54G''). The broadband router is typically configured to act as a firewall and perform Network Address Translation ('''NAT'''). This provides a layer of protection of the internal Local Area Network ('''LAN''') from the outside world. It allows systems on the '''LAN''' to initiate connections to the outside world, but blocks the outside world from initiating connections to systems within the '''LAN'''. | ||
| Line 331: | Line 330: | ||
* Additional services (not typically found on a small broadband router) can be configured. For example, one could setup the '''NST''' system to act as a proxy server for the '''LAN'''. | * Additional services (not typically found on a small broadband router) can be configured. For example, one could setup the '''NST''' system to act as a proxy server for the '''LAN'''. | ||
==== NST Broadband Router Configuration | ==== NST Broadband Router Configuration ==== | ||
The following | The following steps can be followed to configure an '''NST''' probe to act as a broadband router. Using the '''iptables''' firewall creation tool, it can be further configured to specifically allow or block incoming connections from the outside world. | ||
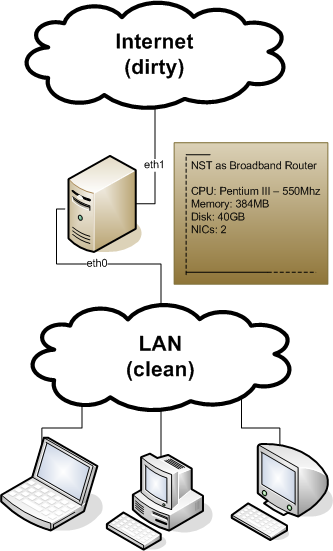
Here is a diagram to give a better idea of how we are using the '''NST''' system in this situation: | Here is a diagram to give a better idea of how we are using the '''NST''' system in this situation: | ||
| Line 339: | Line 338: | ||
[[Image:nst-nat.png]] | [[Image:nst-nat.png]] | ||
==== Step 1: Configure Your NST Box for a Static IP ==== | |||
< | The '''NST''' box acting as the router '''must''' be configured to have | ||
a static IP address by default. In order to do this, create the file: '''/etc/sysconfig/network-scripts/ifcfg-<YOUR NETWORK INTERFACE>'''. | |||
# | Example: | ||
<div class="screen"> | |||
# | <div class="screenTitle">Configuring a Static IP</div> | ||
<div class="userInput"><span class="prompt">[root@probe ~]# </span>cd /etc/sysconfig/network-scripts/</div> | |||
<div class="userInput"><span class="prompt">[root@probe network-scripts]# </span>emacs ifcfg-em1</div> | |||
</div> | |||
The file should have contents similar to the following: | |||
<pre class="programListing"> | |||
DEVICE=em1 | |||
BOOTPROTO=static | |||
IPADDR=192.168.10.1 | |||
NETMASK=255.255.255.0 | |||
NETWORK=192.168.10.0 | |||
BROADCAST=192.168.10.255 | |||
GATEWAY=192.168.10.1 | |||
ONBOOT=yes | |||
NM_CONTROLLED=no | |||
</pre> | |||
==== Step 2: Restart the Network Services ==== | |||
# | <div class="screen"> | ||
# | <div class="screenTitle">Restarting the Network Services</div> | ||
# | <div class="userInput"><span class="prompt">[root@probe ~]# </span>systemctl restart network.service</div> | ||
<div class="userInput"><span class="prompt">[root@probe ~]# </span>systemctl restart NetworkManager.service</div> | |||
<div class="userInput"><span class="prompt">[root@probe ~]# </span></div> | |||
</div> | |||
==== Step 3: Configure & Enable the DCHP Service ==== | |||
Typically, a home router will automatically assign an IP address from a specific range of addresses to any machine that connects to its network. Unless every machine on your '''LAN''' will be given a static IP address, you will need to enable the '''DHCP''' service on your '''NST''' router. Keep in mind that if you are using another router as a switch for your '''LAN''', you must disable its '''DHCP''' service first, so they do not conflict. | |||
The '''DHCP''' service is set up via a configuration file located here: '''/etc/dhcp/dhcp.conf/''' | |||
It is a good idea to make a backup copy of the file before you start working, in case something goes wrong: | |||
# | <div class="screen"> | ||
<div class="screenTitle">Backing up dhcpd.conf</div> | |||
<div class="userInput"><span class="prompt">[root@probe ~]# </span>cd /etc/dhcp/</div> | |||
<div class="userInput"><span class="prompt">[root@probe dhcp]# </span>cp ./dhcpd.conf ./dhcpd.conf.orig</div> | |||
<div class="userInput"><span class="prompt">[root@probe ~]# </span>ls</div> | |||
<pre class="computerOutput"> | |||
dhclient.conf dhclient.d dhcpd6.conf dhcpd.conf dhcpd.conf.orig | |||
</pre> | |||
<div class="userInput"><span class="prompt">[root@probe ~]# </span></div> | |||
</div> | |||
Now open the '''dhcp.conf''' file, delete the old contents, and make an entry similar to the one below. | |||
<pre class="programListing"> | |||
ddns-update-style interim; | |||
ignore client-updates; | |||
get-lease-hostnames true; | |||
subnet 192.168.10.0 netmask 255.255.255.0 { | |||
option routers 192.168.10.1; | |||
option subnet-mask 255.255.255.0; | |||
option nis-domain "your.domain"; | |||
option domain-name "your.domain"; | |||
option domain-name-servers 8.8.8.8; | |||
option time-offset -18000; # Eastern Standard Time | |||
option ntp-servers 192.168.10.1; | |||
range dynamic-bootp 192.168.10.100 192.168.10.150; | |||
default-lease-time 21600; | |||
max-lease-time 43200; | |||
} | |||
</pre> | </pre> | ||
Note that with these settings, every machine in your '''LAN''' will be assigned an IP address of 192.168.10.1xx. Also note that this example uses Google's publicly available DNS server. All these options can be changed according to how you would like to set up your network. When you are done configuring the '''DHCP''' service, enable it by doing the following: | |||
<div class="screen"> | <div class="screen"> | ||
<div class="screenTitle"> | <div class="screenTitle">Starting the DHCP Service</div> | ||
<div class="userInput"><span class="prompt">[root@ | <div class="userInput"><span class="prompt">[root@probe ~]# </span>chkconfig dhcpd on</div> | ||
<pre class="computerOutput"> | <pre class="computerOutput"> | ||
Note: Forwarding request to 'systemctl enable dhcpd.service'. | |||
</pre> | </pre> | ||
<div class="userInput"><span class="prompt">[root@ | <div class="userInput"><span class="prompt">[root@probe ~]# </span>service dhcpd start</div> | ||
<pre class="computerOutput"> | <pre class="computerOutput"> | ||
/ | Redirecting to /bin/systemctl start dhcpd.service | ||
</pre> | </pre> | ||
<div class="userInput"><span class="prompt">[root@ | <div class="userInput"><span class="prompt">[root@probe ~]# </span></div> | ||
</div> | </div> | ||
==== Step 4: Configure IPtables ==== | |||
To enable '''Network Address Translation'''(or '''NAT''') on NST, '''iptables''' must be configured correctly. You can configure '''iptables''' for basic '''NAT''' with the following commands: | |||
<div class="screen"> | <div class="screen"> | ||
<div class="screenTitle"> | <div class="screenTitle">Configuring iptables</div> | ||
<div class="userInput"><span class="prompt">[root@ | <div class="userInput"><span class="prompt">[root@probe ~]# </span>echo 1 > /proc/sys/net/ipv4/ip_forward</div> | ||
< | <div class="userInput"><span class="prompt">[root@probe ~]# </span>iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE</div> | ||
<div class="userInput"><span class="prompt">[root@probe ~]# </span>iptables -A FORWARD -i eth0 -o eth1 -m state --state RELATED,ESTABLISHED -j ACCEPT</div> | |||
<div class="userInput"><span class="prompt">[root@probe ~]# </span>iptables -A FORWARD -i eth1 -o eth0 -j ACCEPT</div> | |||
<div class="userInput"><span class="prompt">[root@probe ~]# </span></div> | |||
</ | |||
<div class="userInput"><span class="prompt">[root@ | |||
</div> | </div> | ||
This will configure your '''NST''' box for basic router functionality. Note that in this state, connections from the outside world will still be accepted. In order to selectively filter incoming and outgoing connections, you will have to configure '''iptables''' further. | |||
Latest revision as of 22:42, 24 April 2013
The following provides some tips and examples of managing the firewall rules at a running NST probe.
In a Nut Shell
- Use quicktables or fwbuilder to initialize your iptables configuration.
- Use iptables-save to save the current configuration as: "/etc/sysconfig/iptables".
- Enable the iptables service.
iptables
The iptables command can be used to manage firewall rules on a NST probe.
Displaying the Active iptables Configuration
The following demonstrates how one can display the current iptables configuration. In the output below, we will see that no firewall rules are in affect:
Chain INPUT (policy ACCEPT) target prot opt source destination Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination
Testing The Firewall Configuration
After adjusting a iptables configuration, one should always verify that the expected behavior is achieved.
- Does the system respond to ping requests as expected?
- Does the system block connection attempts (nmap is handy for this test)?
- Does the system accept connections (if any were configured)?
Testing With Another NST System
The following demonstrates the use of the ping and nmap commands BEFORE any firewall rules have been applied. The commands will be run on the host system named taco and will test the remote NST system with the IP address of: 192.168.0.139:
PING 192.168.0.139 (192.168.0.139) 56(84) bytes of data. 64 bytes from 192.168.0.139: icmp_seq=1 ttl=64 time=2.64 ms 64 bytes from 192.168.0.139: icmp_seq=2 ttl=64 time=0.732 ms 64 bytes from 192.168.0.139: icmp_seq=3 ttl=64 time=2.50 ms --- 192.168.0.139 ping statistics --- 3 packets transmitted, 3 received, 0% packet loss, time 2000ms rtt min/avg/max/mdev = 0.732/1.961/2.648/0.872 ms
Starting Nmap 4.20 ( http://insecure.org ) at 2007-03-04 08:19 EST Interesting ports on 192.168.0.139: Not shown: 65533 closed ports PORT STATE SERVICE 22/tcp open ssh 443/tcp open https 6000/tcp open X11 MAC Address: 00:0C:29:3E:6F:7D (VMware) Nmap finished: 1 IP address (1 host up) scanned in 17.034 seconds
Here's what we see AFTER applying the: "No Incoming Connections" firewall rules (NOTE: This takes a much longer time to complete):
PING 192.168.0.139 (192.168.0.139) 56(84) bytes of data. --- 192.168.0.139 ping statistics --- 3 packets transmitted, 0 received, 100% packet loss, time 1999ms
Starting Nmap 4.20 ( http://insecure.org ) at 2007-03-04 08:24 EST All 65536 scanned ports on 192.168.0.139 are filtered MAC Address: 00:0C:29:3E:6F:7D (VMware) Nmap finished: 1 IP address (1 host up) scanned in 1339.022 seconds
From the Internet
The free "Shields Up!" service at http://grc.com allows one to perform some firewall testing. When a machine is directly connected to the Internet, it allows one to see how the firewall rules will respond when probed from a another machine on the Internet.
Managing iptables As A Service
After one has performed a hard disk installation, it is often desirable to configure the system such that the appropriate firewall rules are loaded at the time the system boots.
The following demonstrates how one can save the current iptables configuration to the file: "/etc/sysconfig/iptables", and enable the iptables service:
Flushing firewall rules: [ OK ] Setting chains to policy ACCEPT: filter [ OK ] Unloading iptables modules: [ OK ] Applying iptables firewall rules: [ OK ] Loading additional iptables modules: ip_conntrack_netbios_n[ OK ]
NOTE: Additional configuration values related to the iptables service can be found in the file: "/etc/sysconfig/iptables-config".
Using quicktables-2.3
Creating configuration files for iptables by hand is a difficult task. The NST distribution comes with the quicktables-2.3 program to help one get started.
No Incoming Connections
The following demonstrates:
- The creation of a script using quicktables-2.3 which will configure iptables such that it does not allow the outside world to connect to your system.
- How to install and list the rules.
- How to save the configuration such that the rules will be enforced the next time the system is started.
running quicktables as the root user is not necessary, and it is not a good idea.
there may not be any particular security reason not to run quicktables as root,
but it's a good practice to get into
press enter to continue or hit the ctrl + c keys to exit:
use this at your own risk. this is supplied without any warranty
stated or implied. this means you're on your own if you use this
software, and that you will not hold the author responsible for any
problems or issues related to the use of this software.
although it isn't required that you run the quicktables script on the
firewall machine itself, it is recommended. quicktables will attempt
to determine the likely answers to many questions simplifying the entire
process. quicktables is really only able to do this when ran on the
firewall machine. when not running quicktables on the firewall machine
itself you may notice things like missing IP addresses in some of the
questions. you will have the opportunity to manually enter any and all
IP addresses that quicktables needs to generate the firewall script
please make sure to read the readme file
iptables was found at /sbin/iptables. is that the location you wish to use in
your firewall script (yes/no) : yes
i have determined that the interface that connects you to your ISP (untrusted
network) is eth0. is this the interface you want to use in your firewall
script (yes/no) : yes
nat, or network address translation, allows you to connect multiple computers on
a private network to the internet using a single internet IP address. if you have
multiple computers and want to use your linux system as a router you need to answer
yes to the next question
would you like to use NAT (yes/no) : no
would you like your internet IP address to be pingable (yes/no) : no
icmp has many messages that are generated by a type field. certain types of icmp
messages have no business coming into the average network. saying yes to the
following question will block incoming icmp types redirect, router advertisement,
router solicitation, address mask request, and address mask reply from the internet.
if you don't know what any of this means then you should also answer yes to the
following question.
would you like to use icmp type restriction to block unwanted icmp types from the
internet (yes/no) : yes
if you run any services on your firewall machine you need to allow connections to their
ports. this option is mostly for standalone non-nat setups or for allowing ident
requests to a nat aware identd running on your firewall. answering no closes all ports
on the firewall machine itself.
would you like to open any tcp ports to the firewall (yes/no) : no
would you like to open any udp ports to the firewall (yes/no) : no
certain networks have been set aside as private networks, and they shouldn't be routed
across the internet. if you're using quicktables as an internet firewall or internet
firewall and nat script then you will want to answer yes to the following question.
if you're using quicktables on a private lan (10.0.0.0/8 172.16.0.0/12 192.168.0.0/16)
then you'll want to answer no to the following question.
do you want to block internet access from reservced private networks (yes/no) : no
blocked hosts will not have access to any ports including those that are open or being
forwarded. hit enter to skip blocking any hosts or networks
enter the ip address(es) and/or network address(es) to completely block. :
logging dropped packets creates a record of the packet. it can also generate a lot of
logging. iptables uses kern.info for syslogging
would you like to log dropped packets (yes/no) : no
squid is a web proxy cache. answering yes to the following question will configure
quicktables to transparently proxy all outbound http requests through squid without
requiring any browser configuration. if you have no idea what this means answer no
to the following question.
do you wish to use squid (yes/no) : no
blocking services will prevent clients on the trusted side of the quicktables machine
from accessing a certain service. a common use for this feature would be to block clients
on your internal network from accessing services like ICQ and P2P services.
if you're uncertain about using this option answer no to the following question.
do you wish to block outbound access to any services (yes/no) : no
your firewall script has been written to rc.firewall
thanks for using quicktables. hit enter to exit.
setting global variables
applying general security settings to /proc filesystem
applying icmp rules
applying icmp type match blocking
applying default drop policies
### quicktables is loaded ###
Chain INPUT (policy DROP) target prot opt source destination DROP icmp -- 0.0.0.0/0 0.0.0.0/0 icmp type 18 DROP icmp -- 0.0.0.0/0 0.0.0.0/0 icmp type 17 DROP icmp -- 0.0.0.0/0 0.0.0.0/0 icmp type 10 DROP icmp -- 0.0.0.0/0 0.0.0.0/0 icmp type 9 DROP icmp -- 0.0.0.0/0 0.0.0.0/0 icmp type 5 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED DROP icmp -- 0.0.0.0/0 0.0.0.0/0 icmp type 8 DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp DROP udp -- 0.0.0.0/0 0.0.0.0/0 udp Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 state NEW
Flushing firewall rules: [ OK ] Setting chains to policy ACCEPT: filter [ OK ] Unloading iptables modules: [ OK ] Applying iptables firewall rules: [ OK ] Loading additional iptables modules: ip_conntrack_netbios_n[ OK ]
Turning an NST Probe Into A Broadband Router
In many homes and small businesses, you will find a small broadband router (such as a LinkSys WRT54G). The broadband router is typically configured to act as a firewall and perform Network Address Translation (NAT). This provides a layer of protection of the internal Local Area Network (LAN) from the outside world. It allows systems on the LAN to initiate connections to the outside world, but blocks the outside world from initiating connections to systems within the LAN.
A NST probe can be configured to act as a broadband router (thus assuming one of the roles of a LinkSys WRT54G).
NST Broadband Router Disadvantages
- Contains moving mechanical parts (more likely to have a hardware failure over time).
- Uses more power.
NST Broadband Router Advantages
- A full suite of Linux tools is available.
- Packet capture can be done on the "clean side" (prior to NAT). This makes network analysis of Internet usage much simpler.
- Additional services (not typically found on a small broadband router) can be configured. For example, one could setup the NST system to act as a proxy server for the LAN.
NST Broadband Router Configuration
The following steps can be followed to configure an NST probe to act as a broadband router. Using the iptables firewall creation tool, it can be further configured to specifically allow or block incoming connections from the outside world.
Here is a diagram to give a better idea of how we are using the NST system in this situation:
Step 1: Configure Your NST Box for a Static IP
The NST box acting as the router must be configured to have a static IP address by default. In order to do this, create the file: /etc/sysconfig/network-scripts/ifcfg-<YOUR NETWORK INTERFACE>. Example:
The file should have contents similar to the following:
DEVICE=em1 BOOTPROTO=static IPADDR=192.168.10.1 NETMASK=255.255.255.0 NETWORK=192.168.10.0 BROADCAST=192.168.10.255 GATEWAY=192.168.10.1 ONBOOT=yes NM_CONTROLLED=no
Step 2: Restart the Network Services
Step 3: Configure & Enable the DCHP Service
Typically, a home router will automatically assign an IP address from a specific range of addresses to any machine that connects to its network. Unless every machine on your LAN will be given a static IP address, you will need to enable the DHCP service on your NST router. Keep in mind that if you are using another router as a switch for your LAN, you must disable its DHCP service first, so they do not conflict.
The DHCP service is set up via a configuration file located here: /etc/dhcp/dhcp.conf/ It is a good idea to make a backup copy of the file before you start working, in case something goes wrong:
dhclient.conf dhclient.d dhcpd6.conf dhcpd.conf dhcpd.conf.orig
Now open the dhcp.conf file, delete the old contents, and make an entry similar to the one below.
ddns-update-style interim;
ignore client-updates;
get-lease-hostnames true;
subnet 192.168.10.0 netmask 255.255.255.0 {
option routers 192.168.10.1;
option subnet-mask 255.255.255.0;
option nis-domain "your.domain";
option domain-name "your.domain";
option domain-name-servers 8.8.8.8;
option time-offset -18000; # Eastern Standard Time
option ntp-servers 192.168.10.1;
range dynamic-bootp 192.168.10.100 192.168.10.150;
default-lease-time 21600;
max-lease-time 43200;
}
Note that with these settings, every machine in your LAN will be assigned an IP address of 192.168.10.1xx. Also note that this example uses Google's publicly available DNS server. All these options can be changed according to how you would like to set up your network. When you are done configuring the DHCP service, enable it by doing the following:
Note: Forwarding request to 'systemctl enable dhcpd.service'.
Redirecting to /bin/systemctl start dhcpd.service
Step 4: Configure IPtables
To enable Network Address Translation(or NAT) on NST, iptables must be configured correctly. You can configure iptables for basic NAT with the following commands:
This will configure your NST box for basic router functionality. Note that in this state, connections from the outside world will still be accepted. In order to selectively filter incoming and outgoing connections, you will have to configure iptables further.