HowTo Use The NST Network Tools Widgets: Difference between revisions
| (110 intermediate revisions by 2 users not shown) | |||
| Line 3: | Line 3: | ||
The '''NST WUI''' includes pop-up network tools widgets for [http://en.wikipedia.org/wiki/IPv4 '''IPv4'''], [http://en.wikipedia.org/wiki/IPv6 '''IPv6'''], [http://en.wikipedia.org/wiki/Hostname '''Host Names'''], and [http://en.wikipedia.org/wiki/MAC_address '''MAC addresses''']. Each '''NST WUI''' pages which display network addresses or host names will allow you to click on the network entity to bring up the appropriate network tools widget. Once the widget is displayed, you can perform a variety of related actions using the network entity. See the [[HowTo_Use_The_NST_Shell_Command_Console | '''NST Shell Console Command Reference Page''']] for supporting information. | The '''NST WUI''' includes pop-up network tools widgets for [http://en.wikipedia.org/wiki/IPv4 '''IPv4'''], [http://en.wikipedia.org/wiki/IPv6 '''IPv6'''], [http://en.wikipedia.org/wiki/Hostname '''Host Names'''], and [http://en.wikipedia.org/wiki/MAC_address '''MAC addresses''']. Each '''NST WUI''' pages which display network addresses or host names will allow you to click on the network entity to bring up the appropriate network tools widget. Once the widget is displayed, you can perform a variety of related actions using the network entity. See the [[HowTo_Use_The_NST_Shell_Command_Console | '''NST Shell Console Command Reference Page''']] for supporting information. | ||
Other network tools widgets for setting [http://en.wikipedia.org/wiki/Domain_Name_System '''DNS'''] overrides globally or for each network interface and a | Each tools widgets has a collection of specific predefined actions that can be executed. An '''NST Shell Console''' output area is attached and used for action results. An '''NST Shell Console Editor''' is also available for command replay and option modifications. | ||
Other network tools widgets for setting [http://en.wikipedia.org/wiki/Domain_Name_System '''DNS'''] overrides globally or for each network interface and a '''[[HowTo Use The NST CloudShark Upload Manager|CloudShark Upload Manager]]''' are available. | |||
= IPv4 Address Tools= | = IPv4 Address Tools= | ||
[[File:Thunderbolt.png|frame|left|'''[[Feature Release Symbol | <center>NST 2.16.0<br /> SVN: 4104</center>]]''']] | |||
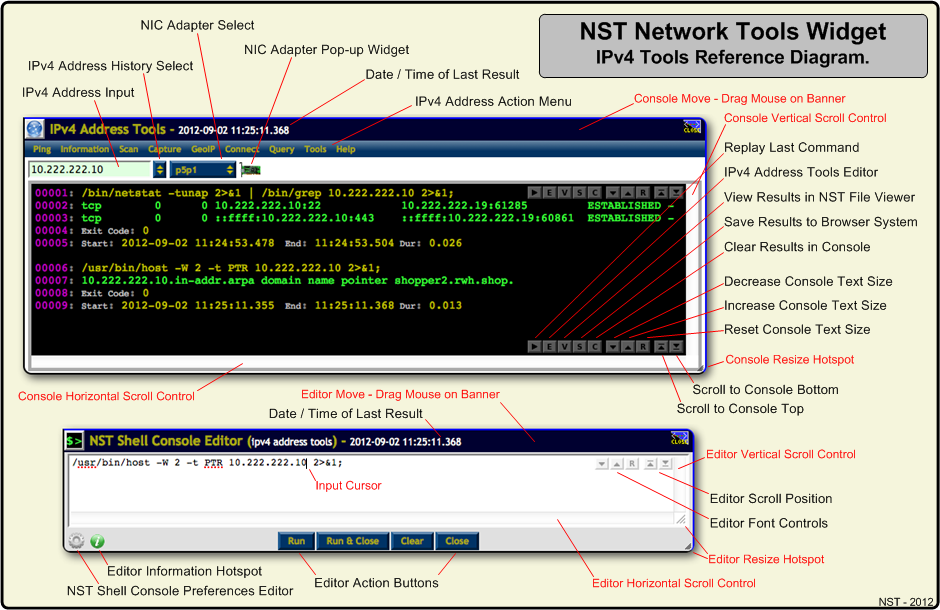
The image below serves as a reference for the '''IPv4 Address Network Tools Widget'''. Common controls can be similarly found on all other '''NST Network Tools Widgets'''. Clicking on most '''IPv4 addresses''' throughout the '''NST WUI''' will bring up this tools widget with the '''IPv4 address''' populated in the input field and ready for an action to be performed using it. The '''IPv4 address''' will be added to your browser session store so that it may be used and selected at a later time with the '''IPv4 Address History Select''' button. | The image below serves as a reference for the '''IPv4 Address Network Tools Widget'''. Common controls can be similarly found on all other '''NST Network Tools Widgets'''. Clicking on most '''IPv4 addresses''' throughout the '''NST WUI''' will bring up this tools widget with the '''IPv4 address''' populated in the input field and ready for an action to be performed using it. The '''IPv4 address''' will be added to your browser session store so that it may be used and selected at a later time with the '''IPv4 Address History Select''' button. | ||
One can also bring up the '''IPv4 Address | One can also bring up the '''IPv4 Address Tools''' widget through the '''NST Navigation Menu''' (i.e. ''Tools'' => ''Network Widgets'' => ''IPv4 Address''). | ||
[[Image:Nsttoolswidget_ipv4ref.png|940px|center|frame|NST Network Tools Widget - IPv4 Reference Diagram]] | [[Image:Nsttoolswidget_ipv4ref.png|940px|center|frame|NST Network Tools Widget - IPv4 Reference Diagram]] | ||
| Line 14: | Line 17: | ||
| | ||
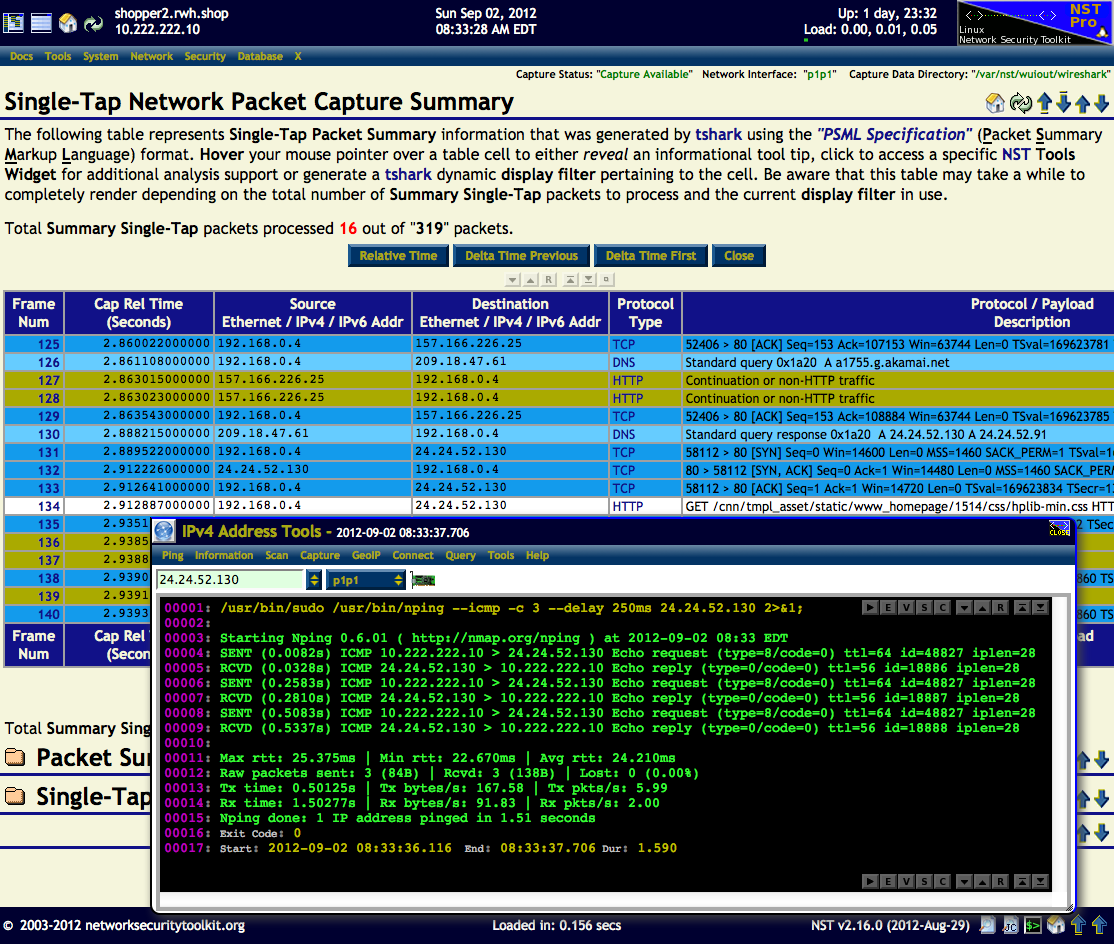
A use case example of the '''IPv4 Address Tools''' widget is shown in action below. The | A use case example of the '''IPv4 Address Tools''' widget is shown in action below. The Destination IPv4 Address: "'''24.24.52.130'''" for Frame Number: "'''134'''" found on this '''Single-Tap Network Packet Capture Summary''' page was ''clicked'' on. The '''IPv4 Address Tools''' widget was then popped up with this address shown. | ||
In this example the '''[http://nmap.org/book/nping-man.html Nmap Network packet generation tool / ping utility]''' (Menu: ''Ping'') was then executed. | |||
[[Image:Nsttoolswidget_ipv4.png|1024px|center|frame|NST Network Tools Widget - IPv4, Action - ICMP Ping to IPv4 Address: 24.24.52.130]] | [[Image:Nsttoolswidget_ipv4.png|1024px|center|frame|NST Network Tools Widget - IPv4, Action - ICMP Ping to IPv4 Address: "24.24.52.130"]] | ||
| | ||
= IPv6 Address Tools = | = IPv6 Address Tools = | ||
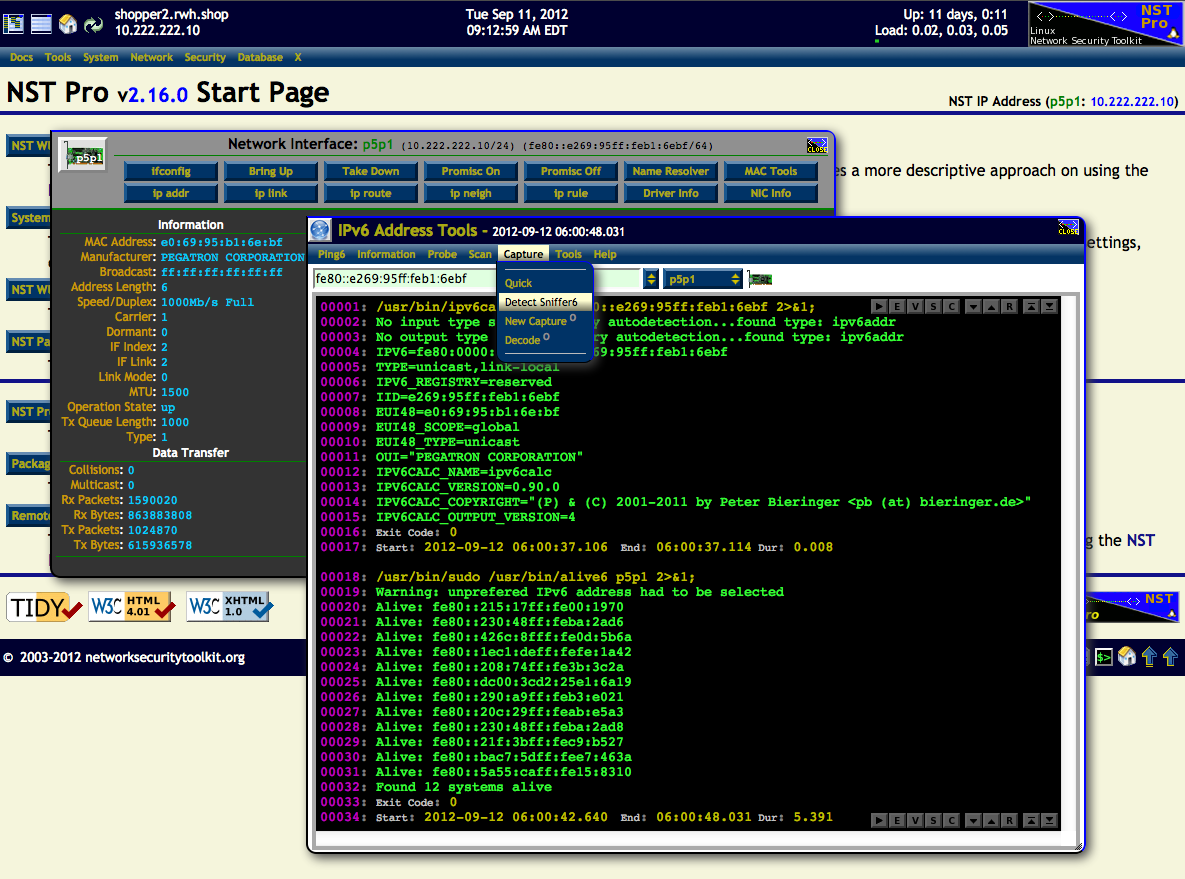
In this use case, the '''IPv6 Address Tools''' widget will be demonstrated. The '''p5p1''' network interface label to the right of the "'''NST IP Address'''" on the '''NST Start Page''' was first ''clicked'' on. This popped up the '''NIC Adapter''' widget for the '''p5p1''' network interface. The IPv6 Address: "'''fe80::e269:95ff:feb1:6ebf'''" located on the '''NIC Adapter''' widget top banner was then ''clicked'' on. This revealed the '''IPv6 Address Tools''' widget. | |||
Firstly, the [http://www.deepspace6.net/projects/ipv6calc.html '''ipv6calc'''] utility (Menu: ''Information'' => ''IPv6Calc'') was used to show information about the '''IPv6''' address. Secondly, the [http://thc.org/thc-ipv6/ '''alive6'''] network utility (Menu: ''Scan'' => ''Alive6'') was used to show all active and responding '''IPv6''' addresses on the network segment for the selected interface: '''p5p1'''. The '''Capture''' menu entries are also shown below with the [http://thc.org/thc-ipv6/ '''Detect Sniffer6'''] tool ''highlighted''. | |||
One can also bring up the '''IPv6 Address Tools''' widget through the '''NST Navigation Menu''' (i.e. ''Tools'' => ''Network Widgets'' => ''IPv6 Address''). | |||
[[Image:Nsttoolswidget_ipv6.png|1024px|center|frame|NST Network Tools Widget - IPv6, Action - ipv6calc: "fe80::e269:95ff:feb1:6ebf" & alive: "p5p1"]] | |||
| |||
= Host Name Tools = | = Host Name Tools = | ||
In this use case, the '''Host Name Tools''' widget will be featured. The '''Active Connections Monitor''' (Menu: ''Network'' => ''Monitors'' => ''Active Connections'') will be used to reveal the '''Host Name Tools''' widget. In this example, the ''green'' host map marker found in the state of Utah, USA was ''clicked'' on. This popped up an information window for this host. The associated fully qualified host domain name: "'''box215.bluehost.com'''" was then ''clicked'' on to bring up the '''Host Name Tools''' widget. | |||
Firstly, the [http://en.wikipedia.org/wiki/Host_%28Unix%29 '''host'''] utility (Menu: ''Information'' => ''Lookup IP'') was used to lookup the '''IPv4''' address for this host name. Secondly, the [http://en.wikipedia.org/wiki/Nmap '''Nmap'''] network utility (Menu: ''Scan'' => ''Nmap TCP'') was used to discover all active [http://en.wikipedia.org/wiki/Transmission_Control_Protocol '''TCP/IP'''] open ports on this host. | |||
One can also bring up the '''Host Name Tools''' widget through the '''NST Navigation Menu''' (i.e. ''Tools'' => ''Network Widgets'' => ''Host Name''). | |||
[[Image:Nsttoolswidget_hostname.png|1024px|center|frame|NST Network Tools Widget - Host Name, Action - Active Connections Monitor Host Information Window: "box215bluehost.com"]] | |||
| |||
= MAC Address Tools = | = MAC Address Tools = | ||
A use case example of the '''MAC Address Tools''' widget is shown in action below. The Source Ethernet (MAC) Address: "'''00:25:f1:71:18:3e'''" for Frame Number: "'''6'''" found on this '''Single-Tap Captured Ethernet Traffic Summary''' page was ''clicked'' on. The '''MAC Address Tools''' widget was then popped up with this address shown. | |||
Firstly, a [http://en.wikipedia.org/wiki/Organizationally_Unique_Identifier '''OUI'''] lookup from the [http://en.wikipedia.org/wiki/Institute_of_Electrical_and_Electronics_Engineers '''IEEE'''] '''OUI NST''' text file: "'''/usr/share/arp-scan/ieee-oui.txt'''" (Menu: ''Information'' => ''OUI Lookup'') was performed. Secondly, a quick capture using the [http://en.wikipedia.org/wiki/Wireshark '''tshark'''] protocol analyzer (Menu: ''Capture'' => ''Quick'') was used to capture packets to and from this ''''ether host'''' address. | |||
One can also bring up the '''MAC Address Tools''' widget through the '''NST Navigation Menu''' (i.e. ''Tools'' => ''Network Widgets'' => ''MAC Address''). | |||
[[Image:Nsttoolswidget_mac.png|1024px|center|frame|NST Network Tools Widget - MAC, Action - OUI Lookup: "00:25:f1:71:18:3e" & Quick tshark Capture: "ether host 00:25:f1:71:18:3e"]] | |||
| |||
= CloudShark Upload Manager = | = CloudShark Upload Manager = | ||
See page: [[HowTo_Use_The_NST_CloudShark_Upload_Manager | '''How To Use The NST CloudShark Upload Manager''']]. | |||
= Default Name Resolver Override Settings = | = Default Name Resolver Override Settings = | ||
The NST network tools widget: "'''Default Name Resolver Override Settings'''" is shown below. This tool can be used by '''NST WUI''' applications that require host name ''resolving''. One can use the widget to override the system default name servers typically found in file: "'''/etc/resolv.conf'''". This can be quite useful when one needs to use an alternative [http://en.wikipedia.org/wiki/Domain_Name_System '''DNS'''] client name server configuration without changing the '''NST''' system default '''DNS''' client configuration. An asynchronous-capable '''DNS''' client utility: [http://www.chiark.greenend.org.uk/~ian/adns/ '''adnsresfilter'''] is used and configured by this widget and by some '''NST WUI''' applications that require a large number of name resolution requests like the [[HowTo_Geolocate_Active_Connection_Information | '''Active Connections Monitor''']]. | |||
The '''Active Connections Monitor''' application also allows for name resolve overriding. The "'''DNS Settings'''" button found in the '''Options''' panel was ''clicked'' on to bring up this widget and is displayed below. You can use the ''Test Resolver'' button to perform a reverse lookup of a '''IPv4''' to verify that your '''DNS''' settings are working as expected. | |||
One can also bring up the '''Default Name Resolver Override Settings''' widget through the '''NST Navigation Menu''' (i.e. ''Tools'' => ''Network Widgets'' => ''DNS Settings''). | |||
[[Image:Nsttoolswidget_dnssettings.png|1024px|center|frame|NST Network Tools Widget - Default Name Resolver Override Settings, Action - Active Connections: DNS Settings Option]] | |||
| |||
= NIC Name Resolver Override Settings = | = NIC Name Resolver Override Settings = | ||
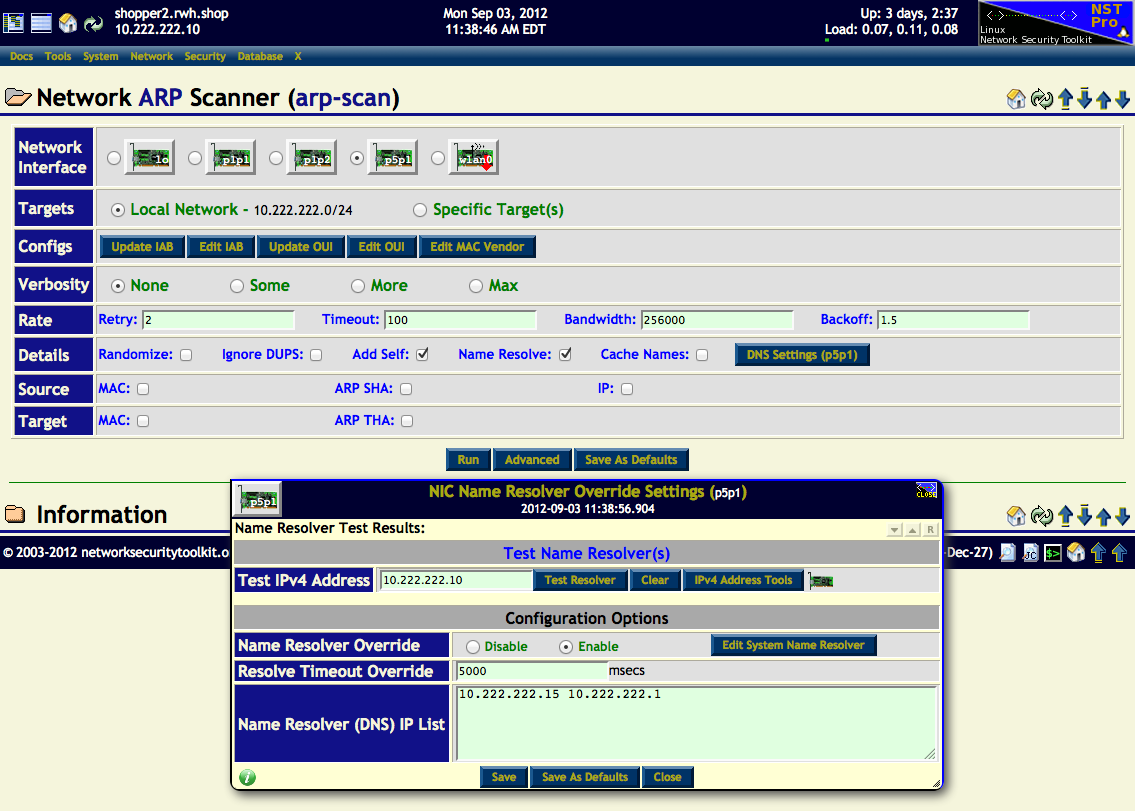
The NST network tools widget: "'''NIC Name Resolver Override Settings'''" is shown below. This tool can be used by '''NST WUI''' applications that require host name ''resolving'' on an individual network segment. One can use the widget to override the system default name servers typically found in file: "'''/etc/resolv.conf'''" for a specific network interface. This can be quite useful when one needs to use an alternative [http://en.wikipedia.org/wiki/Domain_Name_System '''DNS'''] client name server configuration without changing the '''NST''' system default '''DNS''' client configuration on a multi-homed '''NST''' system. An asynchronous-capable '''DNS''' client utility: [http://www.chiark.greenend.org.uk/~ian/adns/ '''adnsresfilter'''] is used and configured by this widget and by some '''NST WUI''' applications that require a large number of name resolution requests like the [[HowTo_Use_The_NST_WUI_arp-scan_Page_To_Quickly_Locate_Hosts | '''Network ARP Scanner''']]. | |||
The '''Network ARP Scanner''' application also allows for name resolve overriding for each selected network interface to be [http://en.wikipedia.org/wiki/Address_Resolution_Protocol '''ARP'''] scanned. The "'''DNS Settings'''" button for network interface: "'''p5p1'''" found in the '''Advanced''' options panel was ''clicked'' on to bring up this widget and is displayed below. You can use the ''Test Resolver'' button to perform a reverse lookup of a '''IPv4''' to verify that your '''DNS''' settings are working as expected. | |||
One can also bring up the '''NIC Name Resolver Override Settings''' widget through the '''NST Navigation Menu''' (i.e. ''Tools'' => ''Network Widgets'' => ''NIC DNS Settings''). | |||
[[Image:Nsttoolswidget_nicdnssettings.png|1024px|center|frame|NST Network Tools Widget - NIC Name Resolver Override Settings, Action - Network ARP Scanner: NIC DNS Settings Advanced Option]] | |||
| |||
Latest revision as of 06:41, 12 September 2012
Overview
The NST WUI includes pop-up network tools widgets for IPv4, IPv6, Host Names, and MAC addresses. Each NST WUI pages which display network addresses or host names will allow you to click on the network entity to bring up the appropriate network tools widget. Once the widget is displayed, you can perform a variety of related actions using the network entity. See the NST Shell Console Command Reference Page for supporting information.
Each tools widgets has a collection of specific predefined actions that can be executed. An NST Shell Console output area is attached and used for action results. An NST Shell Console Editor is also available for command replay and option modifications.
Other network tools widgets for setting DNS overrides globally or for each network interface and a CloudShark Upload Manager are available.
IPv4 Address Tools

SVN: 4104
The image below serves as a reference for the IPv4 Address Network Tools Widget. Common controls can be similarly found on all other NST Network Tools Widgets. Clicking on most IPv4 addresses throughout the NST WUI will bring up this tools widget with the IPv4 address populated in the input field and ready for an action to be performed using it. The IPv4 address will be added to your browser session store so that it may be used and selected at a later time with the IPv4 Address History Select button.
One can also bring up the IPv4 Address Tools widget through the NST Navigation Menu (i.e. Tools => Network Widgets => IPv4 Address).
A use case example of the IPv4 Address Tools widget is shown in action below. The Destination IPv4 Address: "24.24.52.130" for Frame Number: "134" found on this Single-Tap Network Packet Capture Summary page was clicked on. The IPv4 Address Tools widget was then popped up with this address shown.
In this example the Nmap Network packet generation tool / ping utility (Menu: Ping) was then executed.
IPv6 Address Tools
In this use case, the IPv6 Address Tools widget will be demonstrated. The p5p1 network interface label to the right of the "NST IP Address" on the NST Start Page was first clicked on. This popped up the NIC Adapter widget for the p5p1 network interface. The IPv6 Address: "fe80::e269:95ff:feb1:6ebf" located on the NIC Adapter widget top banner was then clicked on. This revealed the IPv6 Address Tools widget.
Firstly, the ipv6calc utility (Menu: Information => IPv6Calc) was used to show information about the IPv6 address. Secondly, the alive6 network utility (Menu: Scan => Alive6) was used to show all active and responding IPv6 addresses on the network segment for the selected interface: p5p1. The Capture menu entries are also shown below with the Detect Sniffer6 tool highlighted.
One can also bring up the IPv6 Address Tools widget through the NST Navigation Menu (i.e. Tools => Network Widgets => IPv6 Address).
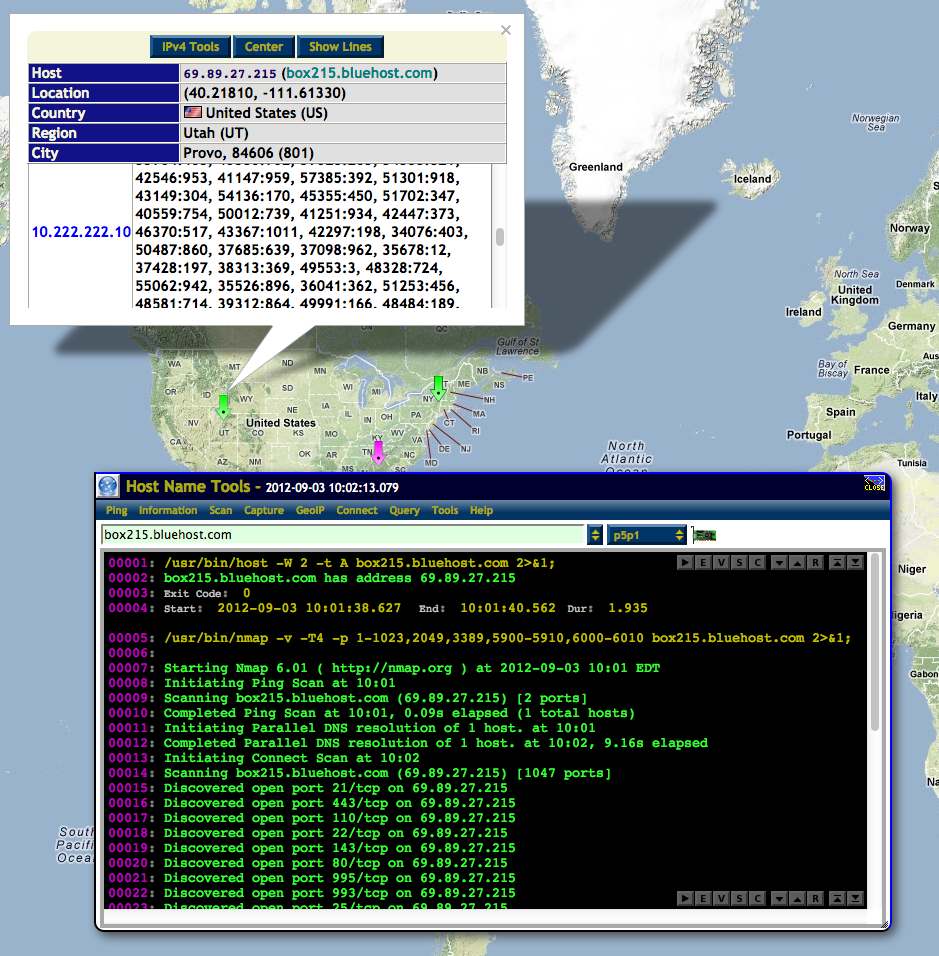
Host Name Tools
In this use case, the Host Name Tools widget will be featured. The Active Connections Monitor (Menu: Network => Monitors => Active Connections) will be used to reveal the Host Name Tools widget. In this example, the green host map marker found in the state of Utah, USA was clicked on. This popped up an information window for this host. The associated fully qualified host domain name: "box215.bluehost.com" was then clicked on to bring up the Host Name Tools widget.
Firstly, the host utility (Menu: Information => Lookup IP) was used to lookup the IPv4 address for this host name. Secondly, the Nmap network utility (Menu: Scan => Nmap TCP) was used to discover all active TCP/IP open ports on this host.
One can also bring up the Host Name Tools widget through the NST Navigation Menu (i.e. Tools => Network Widgets => Host Name).
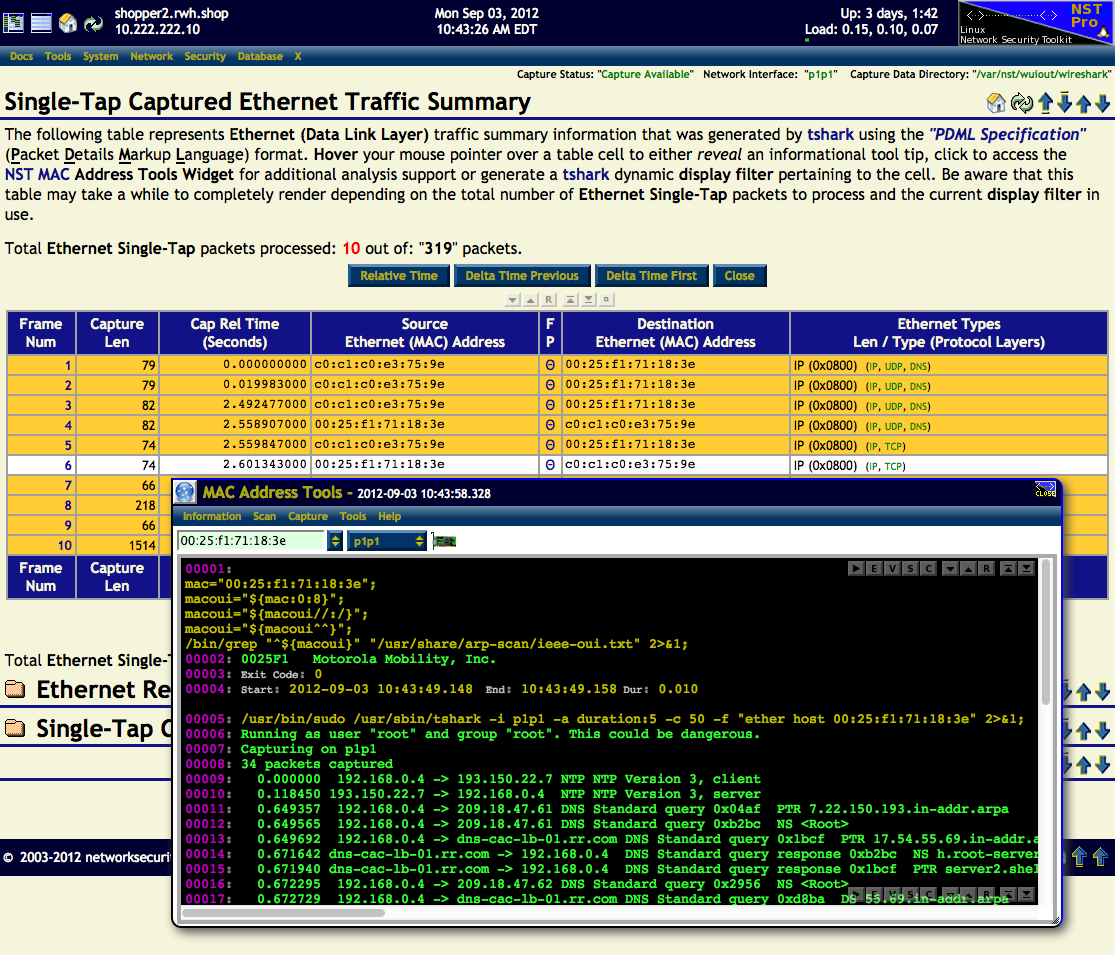
MAC Address Tools
A use case example of the MAC Address Tools widget is shown in action below. The Source Ethernet (MAC) Address: "00:25:f1:71:18:3e" for Frame Number: "6" found on this Single-Tap Captured Ethernet Traffic Summary page was clicked on. The MAC Address Tools widget was then popped up with this address shown.
Firstly, a OUI lookup from the IEEE OUI NST text file: "/usr/share/arp-scan/ieee-oui.txt" (Menu: Information => OUI Lookup) was performed. Secondly, a quick capture using the tshark protocol analyzer (Menu: Capture => Quick) was used to capture packets to and from this 'ether host' address.
One can also bring up the MAC Address Tools widget through the NST Navigation Menu (i.e. Tools => Network Widgets => MAC Address).
CloudShark Upload Manager
See page: How To Use The NST CloudShark Upload Manager.
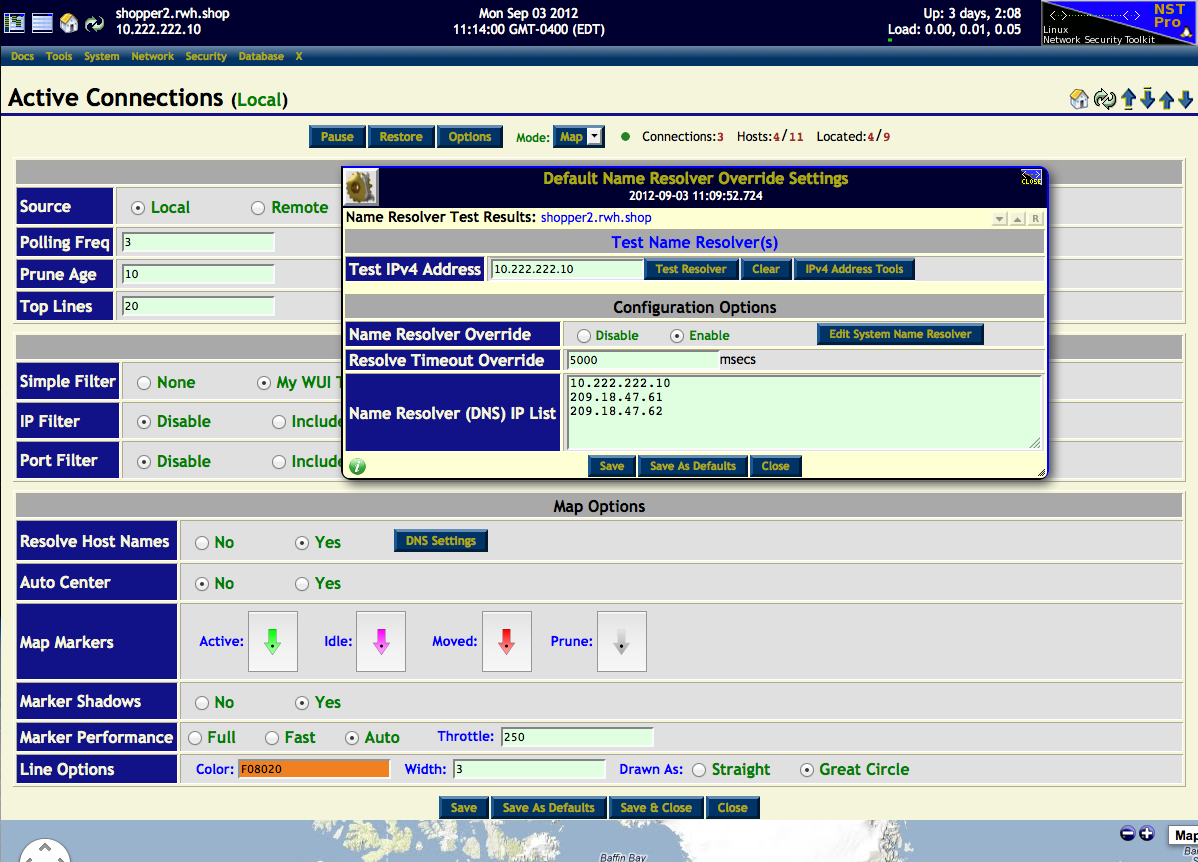
Default Name Resolver Override Settings
The NST network tools widget: "Default Name Resolver Override Settings" is shown below. This tool can be used by NST WUI applications that require host name resolving. One can use the widget to override the system default name servers typically found in file: "/etc/resolv.conf". This can be quite useful when one needs to use an alternative DNS client name server configuration without changing the NST system default DNS client configuration. An asynchronous-capable DNS client utility: adnsresfilter is used and configured by this widget and by some NST WUI applications that require a large number of name resolution requests like the Active Connections Monitor.
The Active Connections Monitor application also allows for name resolve overriding. The "DNS Settings" button found in the Options panel was clicked on to bring up this widget and is displayed below. You can use the Test Resolver button to perform a reverse lookup of a IPv4 to verify that your DNS settings are working as expected.
One can also bring up the Default Name Resolver Override Settings widget through the NST Navigation Menu (i.e. Tools => Network Widgets => DNS Settings).
NIC Name Resolver Override Settings
The NST network tools widget: "NIC Name Resolver Override Settings" is shown below. This tool can be used by NST WUI applications that require host name resolving on an individual network segment. One can use the widget to override the system default name servers typically found in file: "/etc/resolv.conf" for a specific network interface. This can be quite useful when one needs to use an alternative DNS client name server configuration without changing the NST system default DNS client configuration on a multi-homed NST system. An asynchronous-capable DNS client utility: adnsresfilter is used and configured by this widget and by some NST WUI applications that require a large number of name resolution requests like the Network ARP Scanner.
The Network ARP Scanner application also allows for name resolve overriding for each selected network interface to be ARP scanned. The "DNS Settings" button for network interface: "p5p1" found in the Advanced options panel was clicked on to bring up this widget and is displayed below. You can use the Test Resolver button to perform a reverse lookup of a IPv4 to verify that your DNS settings are working as expected.
One can also bring up the NIC Name Resolver Override Settings widget through the NST Navigation Menu (i.e. Tools => Network Widgets => NIC DNS Settings).